Access Control and Flash Loans Among Top Crypto Exploitation Methods in 2022
Notable exploits in 2022 include the Wormhole Hack, Axie Infinity Hack, Nomad Bridge Exploit, and Mango Markets Exploit.

Subscribe to our newsletter!
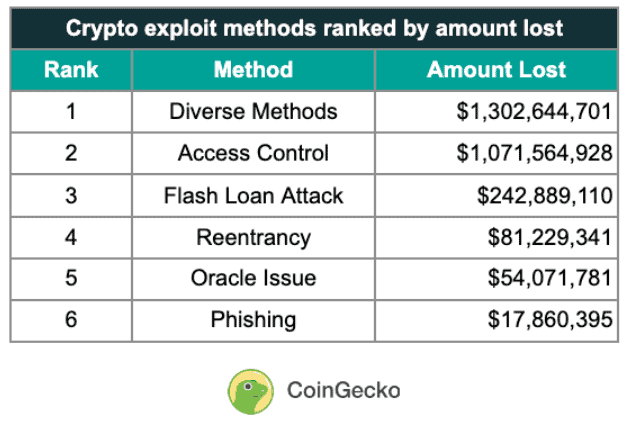
- CoinGecko reports that $2.77 billion was lost to crypto hacks and exploits in 2022, the highest in the past decade, with 47% stolen using unconventional methods.
- Attackers use different methods for crypto hacks and exploits, including Access Control, Flash Loan Attack, Reentrancy, Oracle Issue, and Phishing.
- Notable exploits in 2022 include the Wormhole Hack, Axie Infinity Hack, Nomad Bridge Exploit, and Mango Markets Exploit.
Following the report of 2022 racking the total loss of $2.77 billion due to the hacking and exploiting incidents–the highest in the decade–CoinGecko recently revealed the most damaging methods of crypto hacks and exploits that were utilized last year.
According to CoinGecko, 47% s of $2.77 billion exploited in 2022 were stolen using a diverse range of hacking and exploitation methods such as bypassing verification processes, market manipulation, ‘crowd looting’, taking advantage of smart contract errors or loopholes etc. (read more: Crypto Industry Lost $2.8B Due to Hacks in 2022, Highest in Decade)
“This suggests that crypto hackers are exploring unconventional ways of stealing from projects and users, to get around improving defenses against the more traditional or standard exploitation methods like access control hacking and flash loan attacks,” they noted.
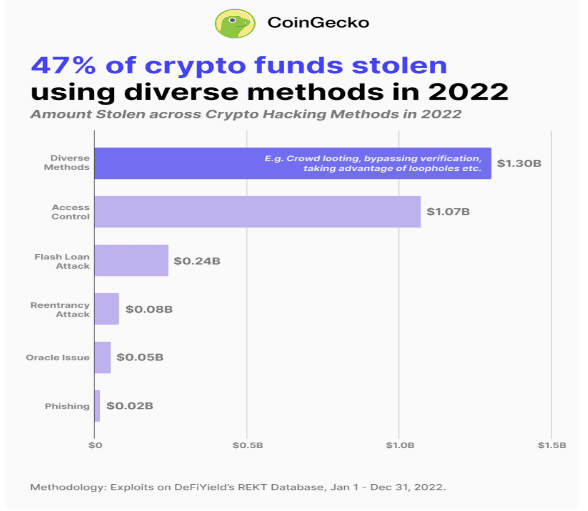
In addition, CoinGecko listed and expounded the different methods that attackers use for crypto hacks and exploits. These include Access Control, Flash Loan Attack, Reentrancy, Oracle Issue, and Phishing.
Exploit Methods
- Access Control
When a private key is compromised, attackers utilize this method to gain access to cryptocurrency wallets or accounts when a private key or gain control over a computer network and its security systems. - Flash Loan Attack
To do this, attackers will borrow a large amount of funds, through loans that need to be repaid within the same transaction and require little to no collateral; then by manipulating a cryptocurrency’s price on one exchange and reselling it on another, the attacker can repay the loan and while they keep the profits. - Reentrancy
For this method, the hackers will use a malicious smart contract that persistently calls the ‘withdraw’ function. And before the exploited contract can update its balance, the cryptocurrency funds there were probably already drained. - Oracle Issue
To be able to exploit accounts and contracts, hackers will first try to gain access to an oracle–which usually supplies price feeds to cryptocurrency protocol, and manipulates the prices provided. Once they succeed, a smart contract failure will follow. At times this will also allow flash loan attacks. - Phishing
Phishing is a form of social engineering where attackers dupe people into revealing sensitive information or installing malware such as ransomware that can gain access to a user’s login credentials or private key.
2022 Exploits
- February
Wormhole Hack
Wormhole, the main bridge connecting Solana to other blockchains, was exploited when it failed to validate ‘guardian’ accounts, which allowed hackers to bypass verifications with a forged signature. The hackers minted and stole $326 million worth of crypto, without needing the equivalent collateral.
- March
Axie Infinity Hack
Axie Infinity, one of the pioneers of the play-to-earn model, had suffered an exploit on its systems, which led to the shutdown of its sidechain Ronin bridge and decentralized exchange Katana. (Read more: Axie Infinity Ronin Network Hack)
The FBI reported that the North Korean hacking group Lazarus is behind the attack on the Ronin Network. According to news site The Block, a fake job ad was what triggered the Ronin hack where the attacker found a backdoor on its gas-free RPC node, which they abused to get the signature for the Axie DAO validator.(Read more: Report Suggests Elaborate Linkedin Job Offer Took Down Axie Infinity)
- August
Nomad Bridge Exploit
Exploiting the crypto ‘crowd looting’ event, the attacker targeted the insecure configuration in Nomad’s smart contract which allowed users to withdraw any amount of funds, without having to prove the transaction’s validity. The looting exploited a total of $190 million.
- October
Mango Markets Exploit
The attacker, Avraham Eisenberg, utilized two accounts and created an artificial inflation within the platform. He sold a large number of perpetual contracts of Mango’s crypto token MNGO from one of his accounts to the other which made the price increase by 1,300 percent in under an hour. After that, Eisenberg used the now-high-priced token as collateral to have a massive loan from Mango Markets $110 million in other cryptocurrencies and then quickly withdrew the funds.
Eisenberg was arrested last December. He was the first person to be arrested by the US authorities for manipulating a decentralized finance (DeFi) trading platform. (Read more: Exploiter Of $110m Defi Project Arrested In Puerto Rico)
This article is published on BitPinas: Access Control and Flash Loans Among Top Crypto Exploitation Methods in 2022
Disclaimer: BitPinas articles and its external content are not financial advice. The team serves to deliver independent, unbiased news to provide information for Philippine-crypto and beyond.