Tracking the Stolen Funds from Ronin Network Using Breadcrumbs
How did the Ronin Network hack took place? Where is the money right now? Lorne Lantz, using the Breadcrumbs tool tracked the blockchain to find out.

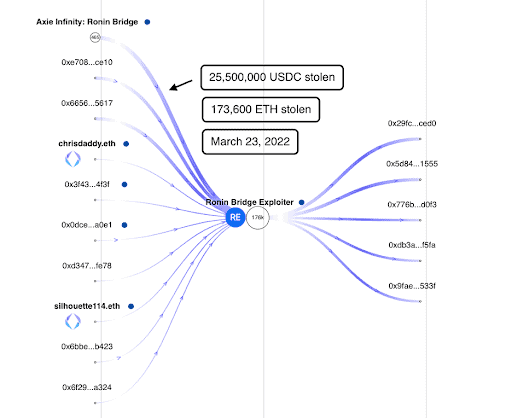
The Ronin bridge was exploited for 173k ETH and 25.5M USDC worth about $590M in cryptocurrencies. The hack took place on March 23, 2022 but it was only made public by the Ronin Network on March 29, 2022.
In this article, we will look into the movement of the stolen funds from the Ronin Bridge to the Hacker’s main addresses:
Main hacker address: 0x098b716b8aaf21512996dc57eb0615e2383e2f96 (https://www.breadcrumbs.app/reports/1266)
Axie Infinity Ronin Bridge address: 0x1a2a1c938ce3ec39b6d47113c7955baa9dd454f2 (https://www.breadcrumbs.app/reports/1267)
https://www.breadcrumbs.app/reports/1266
The hacker’s main address was active on the day of the attack on March 23, 2022, until March 30, 2022. In two transactions, it stole 173,600 ETH and 25,500,000 USDC from the Ronin Network Contract with the following transaction hash:
0xc28fad5e8d5e0ce6a2eaf67b6687be5d58113e16be590824d6cfa1a94467d0b7
0xed2c72ef1a552ddaec6dd1f5cddf0b59a8f37f82bdda5257d9c7c37db7bb9b08
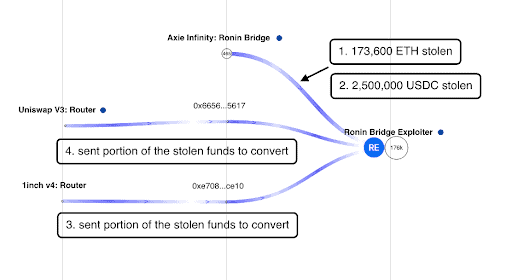
A review of the Hacker’s first transactions showed that after the hack, it interacted with two addresses:
0x665660f65e94454a64b96693a67a41d440155617
0xe708f17240732bbfa1baa8513f66b665fbc7ce10
https://www.breadcrumbs.app/reports/1266
These two addresses were used to swap the stolen funds via Uniswap and 1inch. They swapped the stolen funds into USDC, USDT, DAI and WETH and converted them back to muddy the trail of funds. These two addresses sent the converted funds back to the main Hacker address.
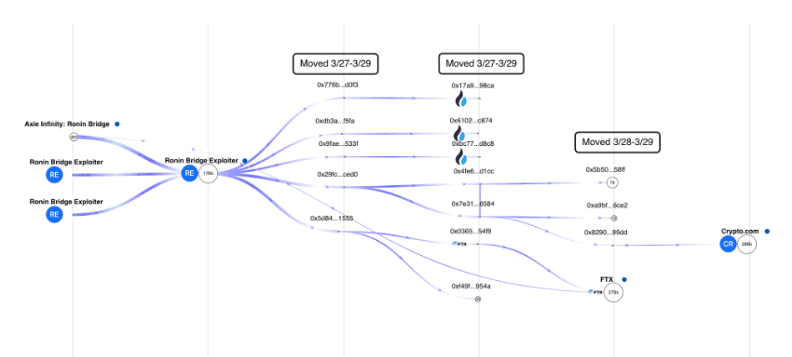
The Hacker waited for four days to move the funds from its main wallet to shell wallets that served as pass through addresses from March 27 to March 29, 2022. It then moved the funds to addresses linked to centralized exchanges such as Huobi and FTX.
https://www.breadcrumbs.app/reports/1266
Since these addresses were only made active during the hack, it can be assumed that these are addresses controlled by the Hacker:
First hop
- 0x776b80e3fd97516ae3a2579cf4eae5ff5867d0f3
- 0xdb3a63562bb7afd44e6b6be8c8269f807c39f5fa
- 0x9fae13de16d34873246e48b514fc88581751533f
- 0x29fc9b71492ec63696cf9cd56e9832a42b0dced0
- 0x5d84a732b355ada31a36b33c446e3dee28f51555
Second hop
- 0x17a96cd2aff8bece22b54a83955fbab5c92a98ca – Huobi
- 0x6102f081de19eb53404b684b4e14667745a4c874 – Huobi
- 0xbc771fb7b6a8876d09fd2e3e2f17fbc91896d8c8 – Huobi
- 0x4fe666ecc5263f5dbb34adb8bc1c8cbb9bbcd1cc
- 0x7e3167771bf23ac10930803589d1424903b36584
- 0x036587e77eabe6a7e181886a5a6ed10dc25654f9 – FTX
- 0xf49fa9956cd53c4581a974a7fd535a15c47b954a
Third hop
- 0x5b5082214d62585d686850ab8d9e3f6b6a5c58ff
- 0xa9bfdc186c6bcf058fbb5bf62046d7bc74e96ce2
- 0x82906886796d110b7ec4c54f6611fb29128699dd
Address on the third hop 0x82906886796d110b7ec4c54f6611fb29128699dd moved the stolen funds to a known Crypto.com wallet: 0x6262998ced04146fa42253a5c0af90ca02dfd2a3
Where are the stolen funds now?
Despite the reported movement of funds, most of the stolen crypto is still on chain sitting in the Hacker’s main address. https://monitor.breadcrumbs.app/dashboard/1452/transactions
Can the hacker be identified?
There is a possibility that the hacker can be identified as it used centralized exchanges to withdraw the funds. Centralized exchanges have Know-Your-Customer policies and programs in place before onboarding a new user and it is likely that the Hacker went through this process to be able to open an account in a centralized exchange.
However, there is also the possibility that the hacker is aware of the thresholds setup by exchanges to not trigger suspicious activity, or the limitations set for non-verified users of centralized exchanges.
This article is published on BitPinas: Tracking the Stolen Funds from Ronin Network Using Breadcrumbs